Tag: Malware detection
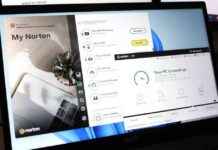
Norton 360 Deluxe Review: Top Value and Strong Protection
Norton 360 Deluxe: A Deep Dive into Protection and Performance Norton 360 Deluxe has established itself as a top-tier antivirus solution, offering robust protection against...
Police operation dismantles Redline and Meta password stealers | TechCrunch
A coalition of international law enforcement agencies recently announced the success of "Operation Magnus," which aimed to dismantle the operations of two notorious infostealers...
AWS Launches Mithra: Identifying and Mitigating Malicious Domains in Massive System
Amazon Web Services (AWS) has unveiled its latest weapon in the fight against cyber threats with the launch of Mithra, a platform designed to...
Cloudflare under scrutiny for hosting abusive websites
Cloudflare, a popular content delivery network, is once again at the center of a debate regarding its role in hosting abusive websites. The company...
Unveiling the Long-Hidden Malware Family on Google Play
A secretive family of Android malware, known as Mandrake, has resurfaced on Google Play after being hidden for over two years. The malware was...
Exploited Proofpoint Email Filter Flaw Sends Millions of Phishing Emails
Cybercriminals have exploited a flaw in Proofpoint’s email relay servers to send millions of phishing emails. The phishing campaign, known as “EchoSpoofing”, began in...
CrowdStrike Attributes Security Update Failure to Testing Bugs: 8.5M Windows PCs Affected
CrowdStrike, a security firm, recently experienced a major issue with its Falcon security software update that affected a staggering 8.5 million Windows PCs. This...
Windows System Crash Caused by CrowdStrike Sensor Configuration Update: Analysis and Impact
A recent system crash in Windows was caused by an update to CrowdStrike sensor configuration, according to reports. The impact of this incident has...
Securing Operating Systems: The Role of Endpoint Security Tools in Disruption
Endpoint security tools play a crucial role in securing operating systems from cyber threats. These tools have become essential in disrupting potential attacks on...